Regional Announcement: ALERT 1: The U.S. Overseas Security Advisory Council (OSAC) has issued a bulletin this week regarding a malicious code that is utilizing Skype in order to gain access to computers. The Asia-Pacific Resource Center, Global IT Team, and World Mission Communications team have spent a significant amount of time researching this issue. Following is a summary of our research:
Overview
- Dubbed T9000
- Currently targets all Windows platforms, (Not MAC at this time)
- Once installed, the code is able to evade many popular antivirus systems including: Sophos, INCAInternet, DoctorWeb, Baidu, Comodo, TrustPort, GData, AVG, BitDefender, VirusChaser, McAfee, Panda, Trend Micro, Kingsoft, Norton, Micropoint, Filseclab, AhnLab, JiangMin, Tencent, Avira, Kaspersky, Rising and Qihoo 360.
- Once installed the software can record Skype calls and upload them along with text chats, an can also take regular screenshots.
- A computer with granted permissions could also have documents stolen, even on removable drives.
- The victim must explicitly allow the malware to access Skype for this particular functionality to work. However, since a legitimate process is requesting access, the user may allow this access without realising what is actually happening.
How It Installs
- The payload is hidden inside spearfishing emails with an infected .rtf document
![]()
- While logged in and operating Skype, user receives a request for explorer.exe to access Skype. It looks legitimate BUT IT IS NOT! Do not allow this request!
- If you are receiving the above notification, the malware has already been delivered to your computer.
Detecting as to whether your computer is infected:
- The procedures for detecting infection are somewhat complex. Antivirus companies are working on resolutions at this time.
- A Google search will reveal multiple sites with steps for removing the involved files. THIS SHOULD BE COMPLETED ONLY BY A COMPETENT COMPUTER TECHNICIAN. Errors here can cause significant damage to your operating system / computer.
Protection:
- Maintain operating firewall and security settings.
- Make sure that antivirus definitions are updated.
- DO NOT open any emails with unsolicited file attachments. Clicking on fake emails and junk attachments can make your PC susceptible.
- Install latest updates to the operating system.
Microsoft’s Response:
- To further protect our customers, we’ve added detection for the malicious software known as T9000 to Windows Defender.
- Customers that have installed security updates released in 2012 (MS12-060) and 2014 (MS14-033), either manually or by enabling automatic updates, will already be protected. Our recommendation is to enable automatic updates, which installs the latest security protections, and to use the latest version of Skype.
ALERT 2: A malicious email is circulating and has already infected at least three computers of personnel on the Asia-Pacific Region. The email will look legitimate because it has your friend’s name and the header shows that it is sent from the legitimate email account. The message will pass through filters undetected because it has all the security signatures of the originating mail server.
The email has the below signature / format:
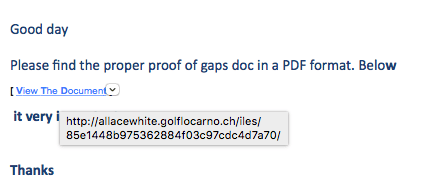
DO NOT CLICK THE LINK “VIEW THE DOCUMENT.”
If you have received this email from a friend, send them an email immediately to the address that you have in your address book (do not simply hit reply) and advise them to change their email account password immediately.
Additional Information:
http://securityaffairs.co/wordpress/44328/cyber-crime/t9000-backdoor-spy-skype.html